Breach Before They Do. Secure, High-Performance Software Development & Penetration Testing.
At Croxec, we help you expose vulnerabilities before attackers do. Our offensive security team simulates real-world breaches through rigorous penetration testing, while our developers build high-performance software engineered to withstand them. No theoretical fixes—just battle-tested solutions that match the speed of modern threats. Get a free initial security assessment and see where you stand.

Enterprise-Ready Security ISO27001, GDPR & SOC 2
At Croxec, we engineer security into every line of code—not just for attack resistance, but for compliance readiness. While we specialize in offensive security, our development process aligns with ISO 27001, GDPR, Chinese Cybersecurity Law, and other frameworks to ensure your software meets regulatory demands. Full certification requires third-party audits, but we’ll give you the technical foundation to pass them. Ask us about our ‘Compliance-Ready Development Package’ to bridge red-team rigor with audit requirements.
Get Your Free Compliance Gap ScanServices
Offensive Security Meets Future-Proof Engineering
Merging red-team vigilance with cutting-edge development to protect what you’re building—and resurrect what you’re stuck with. Whether it’s: building new systems in Rust/Go/Python with exploit-resistant architectures, modernizing legacy apps (.NET, Java) into cloud-native audit-ready deployment, stress-testing everything through black/gray/white box pentests. We ensure your software survives both real-world attacks and compliance audits. No theoretical security—just battle-tested code and actionable results.
Modern Software Development
Bespoke Software Engineering: Built with Rust, Go & Python for Speed + Security
We develop high-performance applications where security isn’t an afterthought—it’s compiled in. Using memory-safe languages like Rust, concurrent systems with Go, and scalable scripting in Python, we engineer software that handles real-world loads while resisting exploits. Ideal for fintech, DevOps tools, and infrastructure needing both speed and armor.
Penetration Testing
Black/Gray/White Box Pentesting: Think Like Attackers, Fix Like Architects
Our red team simulates advanced threats—whether with zero knowledge (black box), some internal access (gray box), or full code visibility (white box). Reports include exploit PoCs and video walkthroughs for your devs to remediate fast.
Code Security Audits
Line-by-Line Security Reviews: Find Vulnerabilities Before Deployment
Our audits combine static analysis (SAST), manual penetration testing, and architectural threat modeling. We’ll flag everything from SQLi risks in your Python web app to unsafe concurrency in Go—with prioritized fixes. Includes a ‘Secure Coding Guide’ tailored to your stack.
DevSecOps Pipeline Integration
Automated Security: Bake SAST/SCANS into Your CI/CD
We harden your GitHub/GitLab pipelines with Semgrep (Python/Rust), GoSec, and custom rules to catch secrets, vulns, and misconfigs before merge. Includes weekly threat intel updates for emerging risks.
CMMC/NIST Compliance Prep
CMMC Readiness: From Zero to Audit-Ready in 90 Days
For defense contractors and federal suppliers, we map your systems to NIST 800-171 controls, run mock CMMC assessments, and prep your System Security Plan (SSP).
Legacy Modernization
Legacy Software Resurrection: Secure, Scalable & Cloud-Ready
Your aging systems are security liabilities and scalability nightmares—but rewriting from scratch is costly and risky. At Croxec, we surgically modernize legacy applications (.NET, Java, PHP) by refactoring monoliths, replacing vulnerable dependencies, automating 80% of testing, enabling cloud migration.
Products
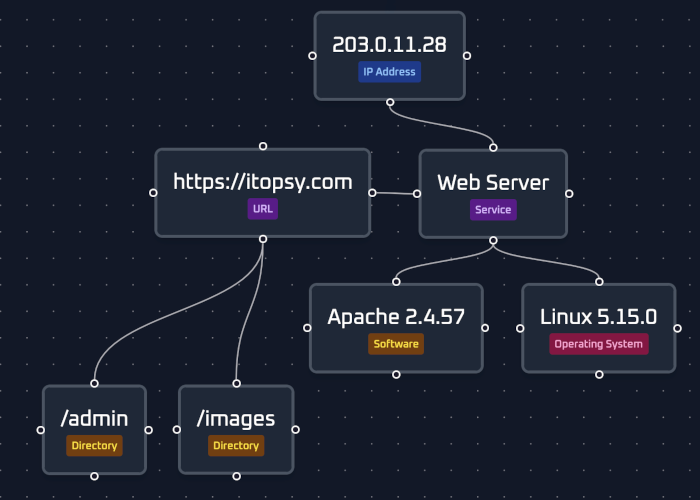
ITOPSY
A node-based ethical hacking platform that empowers internal security teams to conduct professional penetration tests—without offensive expertise—through AI-guided automation, real-time collaboration, and on-premises deployment.
Itopsy platform lets your team run pro-grade pentests without expertise — AI automates reconnaissance and attack mapping, while intuitive workflows replace manual processes. Cut consultant costs and test faster, all with enterprise-level control.
Learn moreContact Us
Ready to test your defenses or build software that fights back?
Our team specializes in real-world attack simulations and high-performance secure development—no fluff, just results. Fill out the form below, and we’ll respond within 24 hours with a tailored plan.
For urgent red-team engagements, email us directly at ops@croxec.com.